Are the days of Virtual Private Networks (VPNs) numbered?
 Tim Compston, Features Editor at Security News Desk, sits down with Mark Ryan, Director of Sales Engineering – EMEA, at leading cloud security provider Zscaler, who warns that vulnerabilities associated with Virtual Private Networks (VPNs) mean that new thinking is urgently required.
Tim Compston, Features Editor at Security News Desk, sits down with Mark Ryan, Director of Sales Engineering – EMEA, at leading cloud security provider Zscaler, who warns that vulnerabilities associated with Virtual Private Networks (VPNs) mean that new thinking is urgently required.
There is little doubt that the way that VPNs operate is at the forefront of topics being debated in cyber and data security circles at the moment. It is, therefore, not too surprising when I speak to Mark Ryan – who runs Zscaler’s pre-sales team for Europe – that this is also playing on his mind. In fact the interview with Ryan comes hot on the heels of a new service that the San Jose, California, based company has just unveiled which, appropriately enough, is called Zscaler Private Access. This, Ryan says, has been designed, specifically, to enable organizations to provide authorized individuals with access to internal applications and their network while, at the same time, strengthening the security of their networks to deter damaging data breaches or other attacks.
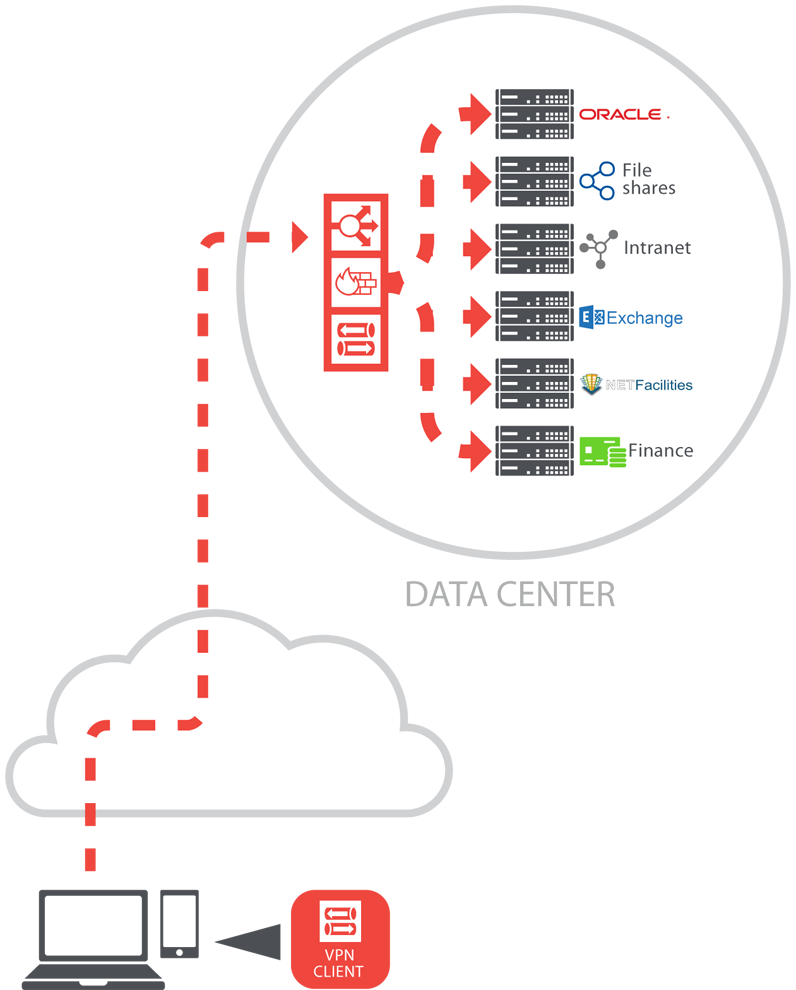
Private accessTalking in more detail about the drivers for those tasked with developing the Zscaler Private Access solution over the past 12 to 18 months, Ryan tells me, that top of the list is the belief that, in today’s rapidly evolving, and increasingly mobile business environment, the traditional route of choice here – a Virtual Private Network – is simply not up to the task: “When you look at the way that stuff has been done in the past, companies have always used a VPN and the problem with a VPN is that it includes the letter ‘N’ which is ‘Network’ – it is a Virtual Private Network. Basically I have a client which runs on my machine and that creates a network tunnel and places me as a roaming user on that network. So I might only need to access one application but I have access to the entire network.” Historical VPN problems
When I ask Ryan if the takeaway from what he is saying – in the context of VPNs – is that the overall access they deliver can be a weak link when it comes to an organisation’s data security he replies in the affirmative. Added to this, Ryan feels that, fundamentally, the VPN concept hasn’t changed much over 20 or even 25 years which, in his view, has exacerbated the situation. In fact the only real step forward he flags up to me is the move to SSL VPN: “Some of the SSL [Secure Sockets Layer]VPNs can do a kind of reverse proxy for web applications but a lot of applications are not web applications so there are a couple of security holes in that. The biggest one being that I am on the network,” says Ryan. Security breaches
Turning to a more detailed discussion about the potential dangers which are out there for organisations, Ryan points me in the direction of a couple of recent high profile data breaches which have exploited VPN-related vulnerabilities. The primary one that comes to mind for Ryan concerns Target, the world’s second largest discount retailer: “When you look at the Target incident in the US they gave a third party access to their network to manage their air conditioning units.” The lesson here, explains Ryan is that when an inspection comes in, like that for air conditioning, because the relevant applications third parties are accessing are not controlled individually, they may unintentionally end up with full access to the wider network.
Of course it is not all doom and gloom for VPNs. Ryan does admit that there are certain things which can be done to mitigate the risks, albeit with a degree of complexity: “There are best practices around when you do a VPN, such as putting people on a specific VLAN [Virtual Local Area Network], and then putting a firewall in and restricting around that firewall what they can access.” However even with this, Ryan reckons that organisations are still having to create a point-to-point link: “This places these remote users, whether they are your own users, or third parties, onto your network to access just the specific application.”
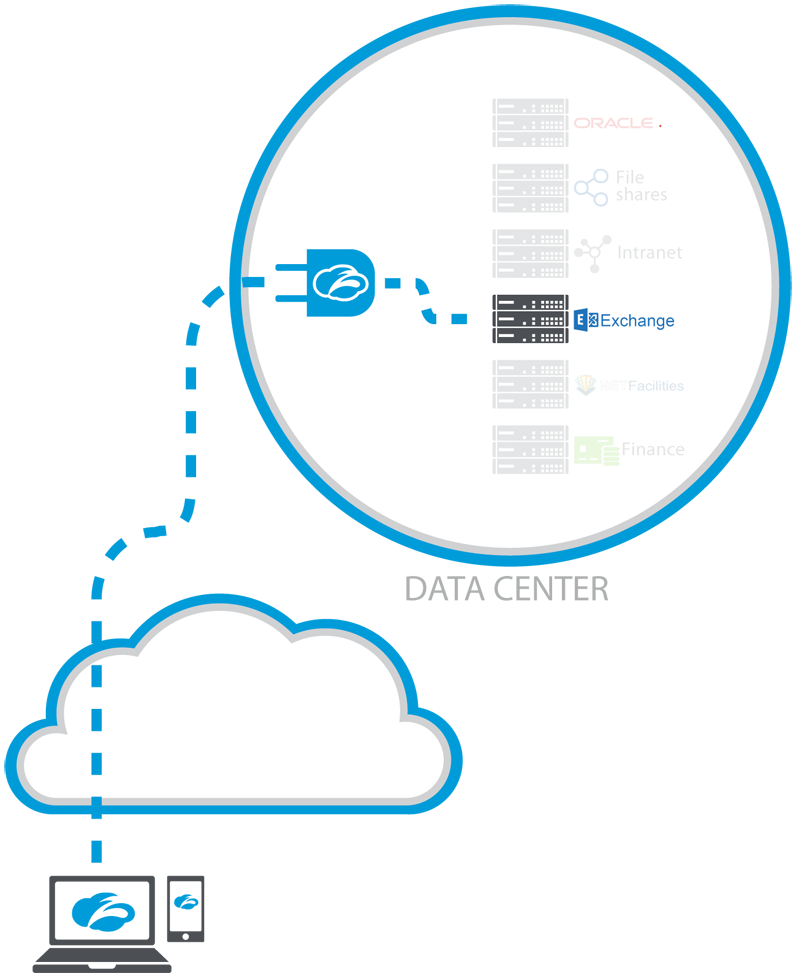
Building on the global cloudSo what is Zscaler doing to address the vulnerabilities which are out there and, significantly, has the potential to mean that troublesome VPNs no longer need to be centre stage? Well, Ryan reveals that the new Zscaler Private Access solution – which was launched at the end of April – has re-written the script here by decoupling applications from the physical network to deliver per user access to ‘apps’ and services running in the internal corporate network, in a data center, or in a public cloud like Amazon. As the service is based on Zscaler’s global cloud there is, Ryan stresses, no requirement for additional hardware or ‘forklift’ upgrades of existing hardware.
Offering more detail on the solution and the thinking behind applying Zscaler’s global cloud infrastructure to make the Private Access route a reality, Ryan says: “With our cloud service we are already present in a hundred data centres around the world to process traffic for users accessing cloud applications. We then said, well can we leverage this cloud architecture that we have built up to provide more granular – application level – access control? When I use the term ‘internal applications’ that means ‘private applications’, applications that are not on the public Internet,” explains Ryan.
Ryan goes on to outline the way that control over access to internal applications is handled within Zscaler Private Access: “You [the organisation] understand who the user is and we understand who the user is, because they are already identified in our cloud platform. We federate users through tools, like Active Directory Federation Services or OneLogin, and have an open ecosystem for authentication via SAML.” As part of the solution, Ryan tells me that a customer installs what Zscaler calls a connector: “This is a lightweight virtual machine that sits inside the network or it can even be inside their public cloud, whether it is Azure or Amazon web-services, or whatever. This connector is orchestrated in the cloud and then as a user accesses an application we are able to stitch these connections together through our cloud and make an end-to-end encrypted connection for those users.”
Ryan is keen to make a clear distinction between what happens with Zscaler Private Access, when the connector is in place, and the VPN scenario: “The connector which is running inside the customer’s network or running inside their cloud is already connecting outbound to the Zscaler cloud and from a security perspective that’s critical because, if you look back at VPNs, a VPN always needed an in-bound connection to a customer’s network whereas these connectors are outbound only.” In practical terms, Ryan stresses that this means that an organisation’s firewall policy is much simpler: “All you are saying is that nothing is allowed inbound.”
According to Ryan a select number of customers have already been trialling the Zscaler Private Access solution for the past 6 to 12 months to great success. This has allowed Zscaler to see how private access works on different desktops and environments and whether this is something that these customers would want to move forward with to replace their VPN client. A comment from Tony Fergusson, IT Infrastructure Architect from MAN Diesel & Turbo – which produces engines for ships and power stations and supports turbo machines – is quite telling in this regard: “MAN have been searching for an alternative to our global VPN solution. In general, legacy VPN technology is extremely complex, doesn’t scale well, and most importantly lacks application-centric security. Traditional VPNs extend the risk to any user that connects, which is a security risk.” He continues: “Zscaler Private Access Control allows me to give users access to a single application and not my entire network.” Protecting internal assets
To conclude, Ryan feels that the new thinking being demonstrated by Zscaler’s solution compared to relying on a VPN is encapsulated by the fact that application access is independent of network access. This means that precious internal assets, essentially, become ‘dark’ to the outside world so, moving forward, unless a user is authorised to access an asset they simply won’t be able to see that it exists and even when a user has access to an application they won’t be able to route back to it.
[su_button url=”https://www.securitynewsdesk.com/newspaper/” target=”blank” background=”#df2027″ color=”#ffffff” size=”10″ radius=”0″ icon=”icon: arrow-circle-right”]For more stories like this click for the Security News Desk Newspaper[/su_button]













