Assessing the insider threat in securing organisations
 Brian Chappell, Director of Technical Services EMEAI, BeyondTrust discusses how best to secure organisations against insider threat.
Brian Chappell, Director of Technical Services EMEAI, BeyondTrust discusses how best to secure organisations against insider threat.
1. What exactly constitutes an insider attack? Is it just employees or anybody who has access to a corporate network?
[BC] – An insider attack comes from within the network, within what’s normally considered to be the trusted environment. The actual threat could come from a user with too much privilege who causes an issue accidentally, a piece of malware launched inside the network (phishing payloads for example), or a malicious user. It’s the opportunity to compromise the network and systems from inside the normal perimeter of the corporate infrastructure.
2. How much of a problem are insider threats to organisations today?
[BC] – Reports such as the DBIR 2015 report indicate that the relative incident counts between insider and external attacks remain largely the same as they have for many years. That doesn’t reflect the risk however as the insider attack often comes with a much greater opportunity to gain access to systems or cause harm than most external attacks. To give a sense of scale, Jérôme Kerviel, a French trader was convicted in the 2008 for forgery and unauthorised use of the bank’s computers, resulting in losses valued at €4.9 billion.
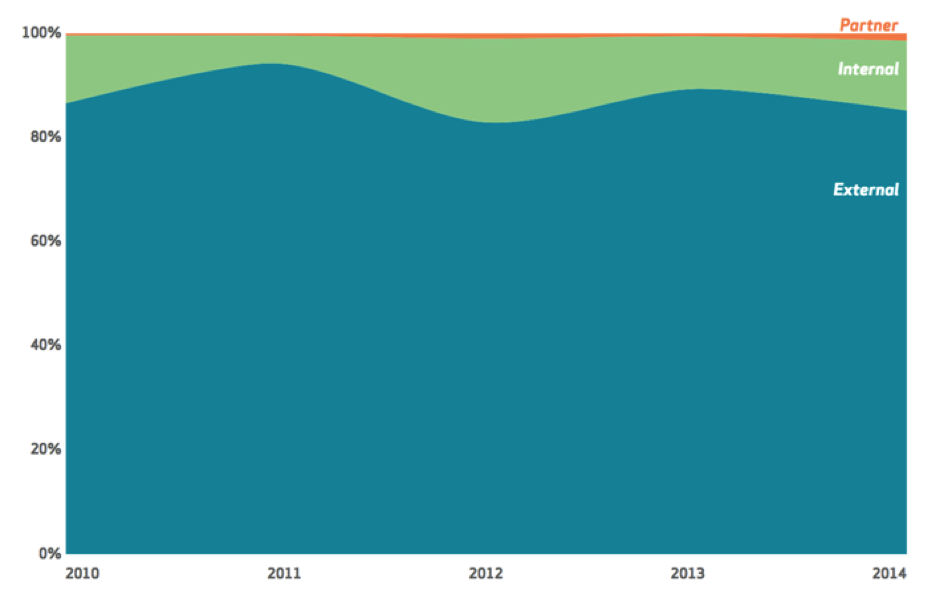
3. Just how prevalent are insider attacks compared to external attacks?
[BC] – The DBIR 2015 report shows a chart (below) indicating that insider attacks constitute around 10-20 percent of all recorded attacks. What we have to bear in mind is that the majority of successful external attacks are successful because of insider risk, i.e. users with excess privilege.
4. To what degree are organisations overlooking the threat of insider attacks?
[BC] – More and more organisations are looking at approaches for tackling insider and external risks which is a shift in the past activity in the ‘Fortress Era’ where firewalls were the mainstay of network security. There are also definite differences in how companies across the world approach the primary concern with insider threat that is often a result of excessive user privilege.
However, all of these approaches I believe are ‘best efforts’, largely because of a lack of awareness of the tooling that’s out there to help. Least privilege as a principle should be the focus as it is entirely possible to have networks with all users as standard users and no direct access to privileged accounts. The awareness is growing and companies are doing the work to adopt this kind of approach.
5. How can insider attacks be detected and avoided from a technology standpoint?
[BC] – The insider attack is somewhat harder to detect than an external as it’s normally performed within the scope of authorised activity with a user account in question being used within the scope of permissions already granted. Behavioural analytics can help here by analysing the supposed legitimate activity looking for patterns which from there is easier to locate and highlight abnormal behaviour.
For example, if John has access to Server A, Server B and Server C but only normally accesses A and C then accessing Server B could be highlighted as abnormal behaviour and may indicate that John’s account has been misused. It may be entirely reasonable behaviour so the first instances of this would logically be labelled as outlier statistically but repeated access in a short period of time strengthens the signal. When you combine this kind of data with data from SIEM systems you can get a clear signal of activity that needs investigation.
6. From more of a people and process standpoint, how can CIOs discourage insider threats?
[BC] – The best approach that any CIO/CISO/IS Manager can take is prevention. The three biggest risks from both an internal and an external perspective are passwords, privilege and vulnerabilities. Address those effectively with Privileged Password Management, Least Privilege and a Vulnerability Management System that targets the vulnerabilities with known exploits first and you’ll be well on your way to securing your environment in both areas.
7. What should be involved in an employee educate programme that aims to eradicate insider threats?
[BC] – The key to user education is an appreciation of the impact of insider compromise. We can talk about the risks but there seems to be a tendency to soften the impact of those risks becoming a reality. This doesn’t mean scaring your teams but it does mean them thinking about the risk when they are working.
For this you need the education to be continuous, more of a dialog and less of a course. We can’t teach everyone to be IT Security professionals but we can include them in the dialog so they know what’s being done and why, how they can contribute to a safer working environment and the continued productivity and success of the organisation.
8. What are the main mechanisms used to gain unauthorised access to systems from within?
[BC] – The biggest risk from an insider perspective is access to privileged accounts, whether directly or via access to passwords. There are still lots of organisations out there with users who have local super-user access to their systems or know the password for one or more shared privileged accounts. In some cases, for ease of use, these passwords can be the same or worse still, stored in easily accessible formats.
I’ve heard of Admin/root passwords being written on whiteboards or scribbled on sticky notes stuck to the users monitor. This is not a situation that has to be, the tooling exists to have every users as a standard user while allowing access to privilege through easily controlled, tightly focused and fully audited mechanisms.
9. How differently do CIOs and CISOs need to approach insider attacks, compared to external attacks?
[BC] – Regardless of job description and reporting line the fundamental approaches need to be the same. IT Security projects need to have the full support of all of the stakeholders, technical and business. At the very basest level we are all working to ensure the organisation can continue to operate efficiently and effectively.
A formal security policy that applies to all is a good method of avoiding super users becoming a weak point with their misguided assumption that the policy does not apply to them.
10. Do you see the situation regarding insider threats getting better or worse? – and why?
[BC] – I would say the situation is getting better but slowly. The awareness of the risk of the insider threat is improving, the understanding of the need to take action is growing.
Realising that many of the risks of an insider threat are also the risks of an external threat is paramount in getting the appropriate focus on the necessary mitigations. We shouldn’t just be looking at the insider or the external threats, the two are linked and addressing both is the only way to properly secure your organisation.
[su_button url=”https://www.beyondtrust.com/” target=”blank” style=”flat” background=”#df2027″ color=”#ffffff” size=”10″ radius=”0″ icon=”icon: arrow-circle-right”]For more information on BeyondTrust click here[/su_button]













