
ICT & Milestone unified with new integrations
Integrated Control Technology (ICT) has released paired integrations between Protege GX, and Milestone’s XProtect platforms.

Integrated Control Technology (ICT) has released paired integrations between Protege GX, and Milestone’s XProtect platforms.

In response to the growing uptake of GlobalPlatform’s Security Evaluation Standard for IoT Platforms (SESIP)

Hannah Larvin, Features Editor of Security Buyer explores how IoT is transforming security with advanced

HID, a provider of trusted identity solutions, announces the acquisition of ZeroSSL, an SSL certificate

GlobalPlatform’s Security Evaluation Standard for IoT Platforms (SESIP) methodology has been adopted as the basis

Hanwha Vision has launched a range of PTZ PLUS cameras with AI capability for accurate

This week the UK government will set out how it’s delivering on its energy security
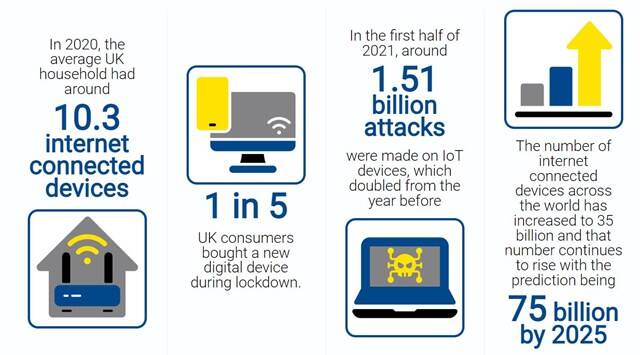
With the Product Security and Telecommunications Infrastructure Act 2022 having now been enacted into law,

The latest edition of the IoT Predictions Report explores how IoT (internet of things) technology

Security Buyer takes a look at some of the biggest trends and predictions for IoT
Copyright notice This website and its content is copyright of Security Buyer – © Hand Media International LTD 2021. All rights reserved. Any redistribution or reproduction of part or all of the contents in any form is prohibited other than the following: you may print or download to a local hard disk extracts for your personal and non-commercial use only you may copy the content to individual third parties for their personal use, but only if you acknowledge the website as the source of the material You may not, except with our express written permission, distribute or commercially exploit the content. Nor may you transmit it or store it in any other website or other form of electronic retrieval system.