The age of Security Analytics, Video Analytics and VCA
Tim Compston, Features Editor at SecurityNewsDesk, discovers how, after a number of false dawns, video analytics or VCA (Video Content Analysis) is coming of age and also investigates the way that sophisticated analytical techniques are now being employed for cybersecurity to pick-up suspicious activity.
Thankfully, the signs are that video analytics really has turned a corner as a growing proportion of CCTV deployments in feature these intelligent solutions, as integral security, safety, and management tools, to deliver the sort of capabilities and accuracy levels that just weren’t possible before. So, in this new era of fit-for-purpose video analytics, we take a closer look at some of the solutions which are coming more into the frame here.
Market moves
Offering a research perspective on the state of play of video analytics, Jon Cropley, Principal Analyst at IHS for Video Surveillance points me in the direction of a whitepaper which IHS issued on the ‘Top Video Surveillance Trends for 2016’. The whitepaper highlights that fact that over the 10 years that IHS has been researching the video content analysis market there has been ‘consistent growth despite various challenges’ and goes on to note that in the latest publication of market data demand for intelligent video surveillance solutions remained strong.
Regarding specific trends coming on stream, IHS reports that there has been a marked swing away from a server-based approach as evidenced in 2014 with the first decline in the market for ‘pure server- based analytics’, with the value of server-based video analytics shrinking by an estimated $39.4 million, in just one year, to $81.9 million. Interestingly this wasn’t a signal that there was a corresponding decline in video analytics market as a whole, in fact the drop-off for server-based solutions was more than offset by a strong rise in edge-based analytics. In the whitepaper on video surveillance trends, the analysts at IHS are not surprised by this change in preference given the heightened processing power on board today’s video surveillance cameras plus lower total system and networking costs.
Tag and track
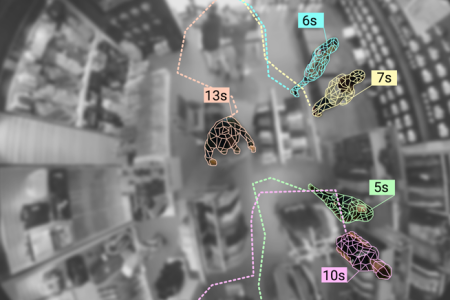
 Pressed on the specific innovations that UK-headquartered Ipsotek is rolling out to push the envelope on video analytics, Technical Director, Dr Boghos Boghossian (pictured left) singles out a capability that he refers to as multi-camera tracking or ‘Tag and Track’ which, in his view, has tremendous potential across a wide array of public space and transportation applications: “This allows a CCTV operator to basically ‘tag’ something virtually which means that on screen they either click on an object, a vehicle, or a person and the analytics will automatically track them across the whole of the surveillance network.” Boghossian says the beauty of ‘Tag and Track’ is that even if an individual leaves the field of view of one camera, and appears in another, the system continues tracking them and, crucially, this process can happen across multiple cameras. He claims that this is an ideal fit for CCTV operations rooms.
Pressed on the specific innovations that UK-headquartered Ipsotek is rolling out to push the envelope on video analytics, Technical Director, Dr Boghos Boghossian (pictured left) singles out a capability that he refers to as multi-camera tracking or ‘Tag and Track’ which, in his view, has tremendous potential across a wide array of public space and transportation applications: “This allows a CCTV operator to basically ‘tag’ something virtually which means that on screen they either click on an object, a vehicle, or a person and the analytics will automatically track them across the whole of the surveillance network.” Boghossian says the beauty of ‘Tag and Track’ is that even if an individual leaves the field of view of one camera, and appears in another, the system continues tracking them and, crucially, this process can happen across multiple cameras. He claims that this is an ideal fit for CCTV operations rooms.
Boghossian confirms that Ipsotek has secured two airport contracts where Tag and Track is a requirement: “One, a VIP airport in the Middle East, has just been completed and deployed and it has 50 channels of Tag and Track and then the other one which we have got the letter of intent and we are going to start deploying it in the latter half of this year it is 1,000 channels of Tag and Track and again this is in the Middle East. For the second one we have completed the test labs so the technology has been approved but we are waiting for them to finish the building.”
Questioning Boghossian about how putting Tag and Track into an airport environment compares to other applications like a city centre, he responds that in some ways it is actually easier: “Most of the time the passengers are following a well-defined route – you go and check-in, you go to immigration, you go to security, you go to duty-free and you go to your gate – and you know the timescale when people need to be where. That is the simpler thing compared to a high street.” What tends to make airports more complicated, reckons Boghossian, is the ‘crowdedness’: “You can get areas which are very crowded in an airport, especially where people are queuing to check-in. On those we have to select the camera locations very carefully so we are capturing people when they are coming out of that crowded space or they are going into that crowded space.”
Accepting analytics
Talking to Gary Mercer, UK Sales Manager at VCA Technology, for his take on why video analytics is more widely deployed today he feels that a combination of things are coming into play: “First and foremost the cost per channel has reduced drastically to around a tenth of what it was eight to 10 years ago. So the cost of having analytics either edge-based or server based per camera is not too dissimilar to the cost of an upper end passive detector.”
Pressed on whether VCA has any preference about where the analytics actually sits: “From a VCA perspective we can do both, however from a market perspective there are more people offering a centralised solution and I think that they have gained some traction over the edge-based simply because installers just see it as an NVR with analytics on it so they have got to install an NVR anyway so they are going to plump for something with these capabilities. The perception in the past was that it was a bit tricky to set a camera up [for analytics] but in reality you still have a camera at the end of the channel, whether you are doing it centrally or edge-based.” Mercer also believes that the other driver for the renewed interest in video analytics is the fact that the manufacturers and re-sellers of analytics have matured: “There is less likelihood of overselling the product which was a real negative in the early days,” reflects Mercer.
Smarter thinking
For his part, Dr Rustom Kanga, CEO at iOmniscient, believes that the footprint of high-end video analytics is likely to expand on the back of a strong focus on smart surveillance applications for urban, highly populated, areas: “There is a growing trend towards ‘smart cities’ where an entire city decides that it wants to have a fully integrated security system. The point is that it is not just about putting in thousands of cameras and saying they are ‘smart’. The key is video analysis and video analysis that works in a crowded scene. Somebody could leave a bag at a bus stop. If it is nice and empty you can pick it up with very simple video analysis however let’s say it is a very crowded area with thousands of people walking in front, that is where you need more advanced video analysis.”
On the question of how video analytics is being re-invented to cope with crowds, Kanga responds that at the ‘high-end’ it requires more than a single element: “Traditional video analysis is built around motion detection, comparing one image with the next, and then if something like a person moves you can say right they have entered the scene. If you have thousands of people then you can’t use motion detection, as everything is moving and every image is different. We have some very unique, intelligent algorithms.” To underline the complexity of the task Kanga reveals that iOmniscient employs about 26 different technologies. One aspect he is happy to offer more detail on is referred to as ‘non-motion detection’: “If a bag is left and everyone is walking around we look at things that stop moving rather than are moving.”
Convergent technologies
Another landmark development, according to Kanga, relates to trying to build things in a more connected and integrated way: “When an operator looks at a bag you need a way for the system to automatically – with one click – highlight who brought it in and then to do a face recognition on that person. It is what we call convergent technologies where you are combining the detection capabilities, the behaviour analysis – someone leaving a bag – along with recognition technology.” As mentioned elsewhere in SecurityNewsDesk Issue 17, iOmnisicent has supplied a solution involving face detection and recognition in a crowd to the Royal Thai Police to automate their policing efforts following the devastating bomb attack last summer on the Erawan Shrine.
Thermal trends
On the subject of video analytics and thermal cameras, Martina Lundh, Global Product Manager for thermal cameras at Axis says that, interestingly, most thermal solutions now feature video analytics from the off: “We really see the benefit of combining thermal with analytics because you don’t have as many false alarms as you might have with visual cameras.” Specifically, she points out, with thermal there isn’t the influence of lighting conditions and the weather.
Considering whether video analytics works best with a particular thermal camera resolution, Lundh says that a determining factor is the processing power available and where it sits, whether that be on or off the camera: “The answer to the resolution question depends on how you use analytics. If it is server-based you can benefit from a higher resolution because you have the processing power to analyse the whole picture, but, in practice, most analytics sits ‘on the edge’ – on the camera – and then, often, you can’t analyse on VGA but may need QVGA or an even lower resolution,” explains Lundh.
Staying with thermal, the desire to build-in analytics was underscored recently when FLIR Systems announced the release of the FC-Series ID thermal security camera in EMEA. This features edge analytics to allow the creation of ‘custom trip wires and regions of interest’ and, FLIR says, is capable of determining human or vehicle intrusions without human intervention.
Retail loss prevention
Demonstrating just how far the potential to detect criminal actions, and errors, around the retail point of sale area has come is the software-based checkout vision system pioneered by StopLift. The state-of-the-art ScanItAll solution automatically analyses CCTV video to interpret the behaviour of a cashier and customer and, crucially, the handling of individual items moving through the checkout area. By mathematically analysing the pixels of digitised video it can be determined if an item has been properly scanned. Apparently this approach is capable of ‘understanding’ a full set of fraudulent behaviours including, for example, when a cashier covers up a bar code by hand or purposely misaligns the scanner and an item. ScanItAll is also claimed to be very effective at detecting refund fraud, basket-based loss, issues at self-checkouts and other operational errors.

Speaking to Malay Kundu, the founder of Cambridge, Massachusetts, based StopLift for his take on the company’s technology, he reveals that part of his background concerned the development of systems to look for terrorists in airports. This is an effort which he reckons has stood him in good stead for the challenging retail environment: “We are applying a lot of really hard-core high tech here. That is how we are able to detect ‘sweet-hearting’ [where there is collusion between employees and customers] and generally scan avoidance. We are doing a ton of this kind of stuff both for manned checkouts as well as now self-checkouts.” On the self-checkout front, Kundu reveals that the company’s technology has found that shoplifting is as much as five times more likely to happen there: “Retailers always suspected that self-checkouts would be highly prone to scan-avoidance.”
 Detecting fire at source
Detecting fire at source
One approach to video analytics where take-up is expected to hot up over the coming year is video-based fire detection in the guise of AVIOTEC from Bosch Security Systems. Building upon Bosch camera technology and Bosch’s Intelligent Video Analysis (IVA), according to the company, AVIOTEC video-based fire detection can supplement other fire detection technologies and enables early detection of smoke and flames in environments where more traditional solutions can’t offer satisfactory reaction times such as buildings with high ceilings or dusty and humid areas. AVIOTEC can also secure environments, points out Bosch, where no other solutions exist, for example saw mills or paper factories, hangars or extremely large monitoring areas.
A key benefit of AVIOTEC, Bosch reckons, is the way that it can employ intelligent algorithms in CCTV cameras to identify smoke and flames as soon as they come into the range of the camera instead of having to wait for smoke to migrate to smoke detectors. By detecting fires at the source rather than the ceiling, cameras can issue an alarm within seconds while for point detectors it can take minutes to detect an alarm condition. AVIOTEC is based on intelligent algorithms to distinguish between real fires and other factors like reflections, movements or backlights, to support reliable detection with almost no false alarms.
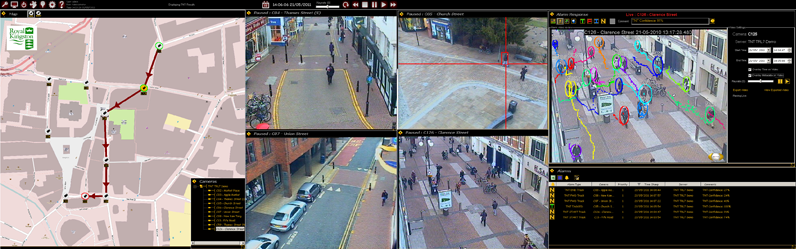
VCA analytics tracks success at Wuxi East railway station
 VCA Technology feels that the recent installation of an integrated video surveillance system at Wuxi East Railway Station in China is an excellent example of how video analytics can encompass security and people counting to help the railway sector introduce efficiencies and save lives.
VCA Technology feels that the recent installation of an integrated video surveillance system at Wuxi East Railway Station in China is an excellent example of how video analytics can encompass security and people counting to help the railway sector introduce efficiencies and save lives.
The Wuxi East Railway Station is served by the 1,318-kilometre long Beijing–Shanghai high-speed railway, the busiest line in China and the world’s longest high-speed line ever constructed in a single phase. A decision was made by the station’s senior management to invest in an integrated system that could take advantage of the latest advances in video surveillance and alarm technology.
A key requirement of the system was the ability to detect and create alerts should a member of the public attempt to enter a restricted area of the station or climb down onto the rail tracks. Despite the obvious danger of being struck by a train entering or leaving the station, there had been several situations where people had crossed the tracks since the high-speed line was officially opened in 2011. In addition to security and safety requirements, it was also specified that the integrated system must be able to supply statistical data on the numbers and flow of passengers that enter the station.
Multi-tasking VCA analytics
VCA Technology in Wuxi won the contract to install the integrated system, which utilises high definition IP network cameras with VCA analytics on-board. The power and flexibility of the VCA analytics engine is able to perform both security and people counting functions, using a single set of ‘rules’ that reflects the operational requirements of the station.
VCA analytics is also able to detect people who trespass into restricted areas. When these situations occur, the analytics has been configured to send SMS and email alerts to security personnel and station platform staff, as well as trigger audio warning messages over the station’s PA communication system.
“There are so many elements of an integrated system that need to perform well in order to meet the demanding requirements of an important project such as this. It has been a major advantage that we have been able to single source the analytics required for security and people counting purposes.” said Bin Cheng of VCA’s Wuxi office.
Analytics in action for cybersecurity
Of course security analytics is much more than just video analytics associated with CCTV systems, in these days of rising cybercrime analytical techniques are being employed to pick-up in suspicious activity in the virtual world as well.
Carmina Lees, Director of IBM Security in the UK and Ireland, stresses that as clients ‘apply cognition’ to transform their business, they will generate even more data: “A greater variety of data that is highly personalised and valuable to their customers as well as hackers. Securing a Cognitive Business requires an immune system-like defence, including advanced analytics to detect and thwart threats, similar to the antibodies that fight disease; and a sharing of cyber-threat intelligence between the public and private sector, similar to how global health organisations collaborate on disease outbreaks.”
One significant IBM development on the horizon which Lees flags up is that it is beginning to see how Watson – a technology platform that uses natural language processing and machine learning to reveal insights from large amounts of unstructured data – can fight cybercrime: “We recently started by training Watson advisors to understand the language of cyber security, which will help security professionals gain insights from massive amounts of cyber threat data via simple language queries.”
The analytics approach to security, Lees adds, is something that IBM has been the leader in for years: “In fact, Gartner recognises IBM Security as the number one leader in security intelligence. QRadar, our security intelligence platform, does this for thousands of companies around the world by bringing in hundreds of thousands of events every second, running analytics to identify unusual activity and behaviours.” Lees cites the example of Wimbledon: “During The Championships, IBM QRadar detects and block thousands of suspicious events, providing AELTC with a unified view of all security events, and applies real time analytics to rapidly identify and address potential attacks.” In the first five months of last year (2015), IBM observed a 94 percent increase in the number of cybersecurity events managed by IBM on the wimbledon.com infrastructure compared to the same period in 2014.
Cloud concerns
 For Ed Macnair, CEO of CensorNet – the cloud security specialist – says that analytics is absolutely critical to what the business does: “It is all very well to try and block threats or block specific user activity but unless you actually understand what is happening in the wider context you are still flying blind in effect.” Macnair adds that one of the things that CensorNet does is to look at all in-bound and out-bound communication for an organisation ‘holistically’: “So whether that is web traffic, email traffic or even application traffic, all of that traffic and effectively pick out what we see as malicious or harmful behaviour and this really sort of ties in very strongly to having a ‘big data’ engine or a big data backend effectively where we are able to collate millions of events and correlate that activity.” He points out that it is difficult when you have one incident of one person accessing an app in isolation: “For that you have got to apply some intelligence to it so for example if you see somebody downloading your customer list from a CRM tool that on its own may or may not have a risk profile but the normal activity for access by a sales force person is between 6.00 am and 8.00 pm and he normally accesses it from London and all of a sudden this is coming in at 3.00 am and is from China it might have a very different risk profile,” concludes Macnair.
For Ed Macnair, CEO of CensorNet – the cloud security specialist – says that analytics is absolutely critical to what the business does: “It is all very well to try and block threats or block specific user activity but unless you actually understand what is happening in the wider context you are still flying blind in effect.” Macnair adds that one of the things that CensorNet does is to look at all in-bound and out-bound communication for an organisation ‘holistically’: “So whether that is web traffic, email traffic or even application traffic, all of that traffic and effectively pick out what we see as malicious or harmful behaviour and this really sort of ties in very strongly to having a ‘big data’ engine or a big data backend effectively where we are able to collate millions of events and correlate that activity.” He points out that it is difficult when you have one incident of one person accessing an app in isolation: “For that you have got to apply some intelligence to it so for example if you see somebody downloading your customer list from a CRM tool that on its own may or may not have a risk profile but the normal activity for access by a sales force person is between 6.00 am and 8.00 pm and he normally accesses it from London and all of a sudden this is coming in at 3.00 am and is from China it might have a very different risk profile,” concludes Macnair.
[su_button url=”https://www.securitynewsdesk.com/newspaper/” target=”blank” style=”flat” background=”#df2027″ color=”#ffffff” size=”10″ radius=”0″ icon=”icon: arrow-circle-right”]For more stories like this click here for the SecurityNewsDesk Newspaper[/su_button]