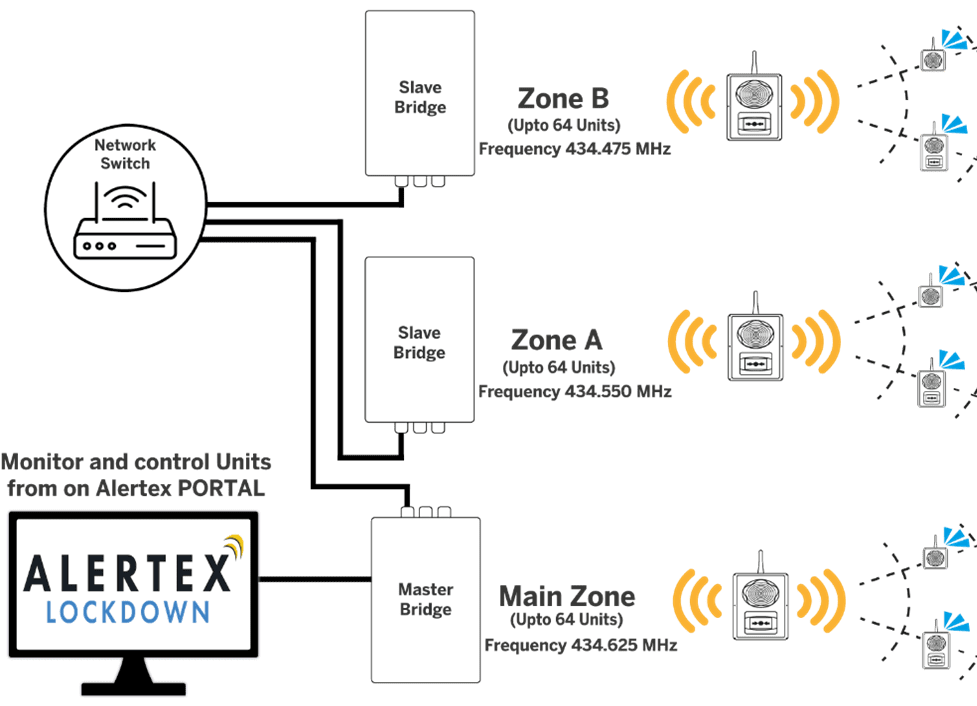
DuoKey will unveil its groundbreaking use case for encrypted financial intelligence at GISEC Global in Dubai next week. Designed to address the challenges of fraud detection and regulatory compliance, this approach, which combines Fully Homomorphic Encryption (FHE) and Multi-Party Computation (MPC)-based Key Management (KMS), allows financial institutions to analyse encrypted transactions in real time without ever decrypting sensitive data.
In a global financial landscape where illicit transactions exceed $2 trillion annually and compliance fines topped $10.4 billion on a yearly basis according to the United Nations Office on Drugs and Crimes, DuoKey confidential AI use case for the financial sector demonstrates how financial institutions can securely process high-risk transaction patterns, perform watchlist screening and assess customer risk profile, while preserving end-to-end encryption and maintaining jurisdictional data control.
“Traditional approaches expose data during analysis, creating systemic security gaps,” said Nagib Aouini, CEO of DuoKey. “Our use case shows how FHE and MPC-based KMS together allow financial institutions to detect fraud, meet AML obligations and collaborate securely without any compromise on data confidentiality or sovereignty.”
DuoKey financial intelligence solution enables secure collaboration between banks, regulators, and fintech providers by allowing cross-border investigation and compliance workflows without revealing underlying customer data. This addresses a longstanding roadblock to industry-wide fraud detection while complying with privacy and regulatory standards such as GDPR, FATF, and PCI DSS.
Visitors to GISEC Global will get the opportunity to explore the live use case at the DuoKey booth (D-120, Hall 6) starting on May 6 until May 8. Schedule your personalised demo at GISEC Global to see how DuoKey financial intelligence enhances fraud detection and compliance. Demonstrations include real-time transaction scoring, encrypted rule-based screening and dynamic anti money laundering (AML) analytics all with performance benchmarks that rival traditional unencrypted systems.