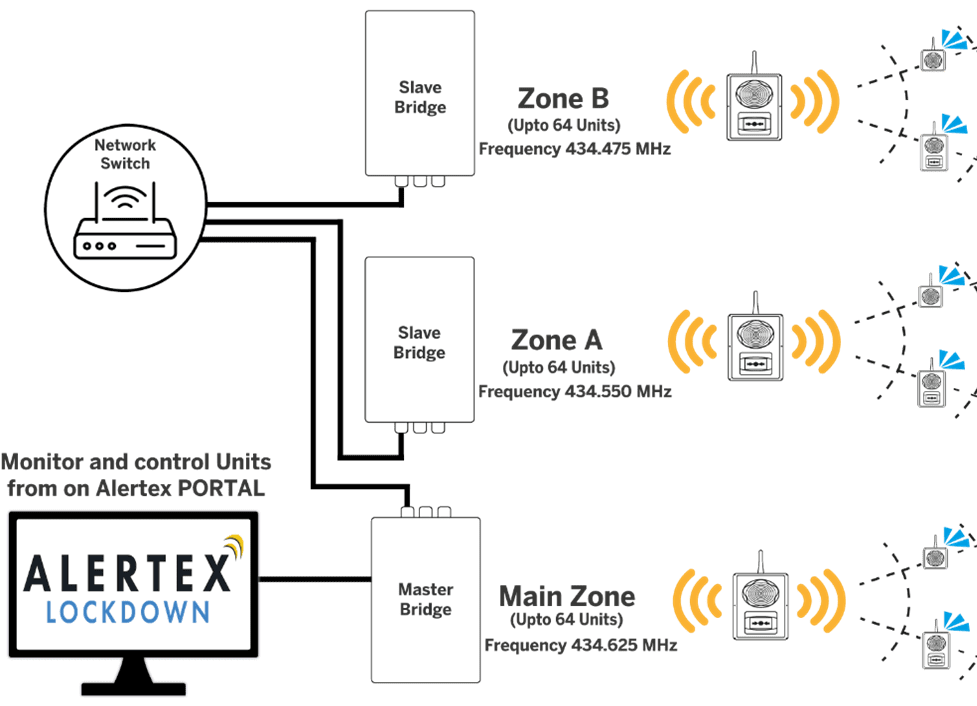
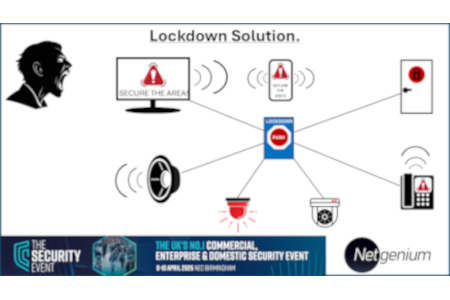
As schools and universities gear up for a new term, John Convy, Principal, Convy Associates, looks at campus security management.
Since the tragic incidents that occurred in the Unites States in Columbine, University of Arizona, Virginia Tech, and Sandy Hook in Connecticut, sociologists have analysed campus violence, hoping to prevent it. And a number of technology firms are marketing integrated identity management and security solutions specifically to colleges and universities. Some of these unique applications developed for higher education may lead to broader, industry-appropriate solutions that will eventually filter into other market segments. This strikes me as an interesting domain for other security professionals to watch and learn from, especially those involved with capitol campuses and other government complexes.
“The first step in reducing risks from intruders on higher education campuses is to implement an integrated identity and rights management system,” suggests Mat Birnbaum, Vice President of Technology at IDENTIGY. “This should be a comprehensive system of record for the institution and the government entity responsible for overall campus security. It should verify people’s identities in real time, and define the roles, permissions, rights, and activities they are authorised for within the perimeter, at any given time.”
Knowing every person on campus, enrolling them in a system that tracks relevant information — including activities and whereabouts — gives security people a clearer picture of what is happening in real time.
Identity data captured from a credential card or smart phone can be sent and displayed in either a math-based interface, metrics dashboard, or drilled down to focus on a specific person of interest being vetted by security personnel. This enables tighter control of perimeters and knowledge of exactly who is on campus in the event of an emergency notification. It also provides a way to account for people, muster them when needed, and control entry and exit to buildings and internal perimeters.
“Step two is to control entry/exit points with electronic security in the form of access control and video surveillance,” Birnbaum explained. “Apply technology solutions to what’s typically a very porous and uncontrollable situation by associating people and vehicles to a trackable identity at all the entry points, with video cameras, access control cards and biometrics. Then create a perimeter with systems that can be alarmed, triggered, and displayed to command centres and mobile responders, using video and other information.”
When the system recognises a pre-defined condition, a response can be executed automatically. For example, if a blacklisted vehicle is detected driving onto campus, the automation could put the campus in lockdown through access control, send notifications to administrators and first responders, or implement whatever degrees of severity the institution wanted to undertake in response to a specific scenario.
When every student and faculty member carries a smart phone with an app—if they see a threat, they can push a button and send a photo of the scene. You don’t have to wait for a police officer or security person to arrive on scene to sound an alert.
“Step three is enabling collaboration and sharing of a common set of information in response to an event,” Birnbaum added. “Making data available to those who need it, whether it’s an event condition, alarm condition, or a real time photo from the scene. Some responders might arrive in squad cars and they need to view information on mobile data terminals, tablet PCs or smart phones. Foot patrol guards will likely be carrying smart phones. Dispatch centers typically have video walls, and a resident advisor at a desk in a residence hall may be using a desktop or notebook computer. The idea is to get information out to all of the interested parties at the same time, so that everybody can collaborate and execute tasks such as firing up communication channels, so that everybody can speak to each other in real time, no matter what device they are using – a radio, landline phone, IP phone, cell phone, or whatever.”
Full campus security implementations can be extended to include health and personal safety. A person might be down somewhere – someone is sick, they have food poisoning, or they’re experiencing seizures. An event could be anything that requires the attention of safety officials, medical personnel, or administrators.
Tools and apps can be provided to students who are uncomfortable, for example, walking back to their car late at night from the library, or walking through a rough part of town near campus. They can press a button that says, “Follow me,” and they’ll appear on a map in the dispatch center with their current position and destination marked. If they deviate from their route or suddenly start traveling at 40 miles an hour, having possibly been abducted and in a moving car, or they stop for too long a period of time, alerts are sounded and appropriate actions can be initiated.
|
Solutions offered by various identity management vendors and sold into higher education enable access control, integrated security, campus ID card privilege control, housing services, food service, catering, nutrition services, online ordering, and other campus-wide activities.
Secure credentials can also be used for common conveniences, such as using student aid funds to purchase goods and services – cafeteria meals, vending machine items, taxicab service and printing are common examples. If a student misplaces or forgets to carry an ID/credentialing card, a text message can be sent from the student’s cell phone to receive instant building or room access using a feature known as “Open My Door,” reducing the need for middle-of-the-night visits by security or residential staff.
John Convy has over 20 years of experience in the technology industry. John is the principal consultant at Convy Associates, which provides strategic alliance and lead generation programs that monetize relationships and accelerate demand for security manufacturers.
Prior to Convy Associates, John was Senior Vice President of Strategic Alliances at BRS Labs. Before that, he created the Technology Partner Ecosystem Program for Cisco’s Physical Security group with over 60 global partners. Prior to that, John directed Strategic Communications for BroadWare Technologies, which was acquired by Cisco in July 2007.
John is the founder and managing director of both the “IP Vide Surveillance Academy” and the “Open Standards Security Alliance”, which promote the open architecture, standards-based security model, and produce educational seminars that have drawn thousands of attendees. He is also a frequent speaker at global security industry events.
Prior to his involvement in the security industry, John founded a political technology company – Grassroots Systems Inc. in 1989, and served as President until its sale in 2000.
John Convy and Convy Associates provide strategic alliance, A&E consultant, technology ecosystem, and lead generation programs to monetise relationships and accelerate demand for leading security industry manufacturers. John is the Founder and Managing Director of the Open Standards Security Alliance and the IP Video Surveillance Academy, and is a speaker at many global industry events.