From evolution to revolution with physical and cyber security solutions
Tim Compston from Security News Desk finds out how security solutions have been geared up to meet ever-evolving challenges.
Many of today’s mission-critical security solutions are a far cry from what was fielded even ten years ago thanks to unprecedented, fast-paced, advances in technology and, crucially, the lessons learnt from the battle against terrorists – and criminals – seeking to exploit vulnerabilities in physical and cyber defences.
Stopping power
When talking about measures that represent the first line of defence against a determined vehicle-borne terrorist attack, hostile vehicle mitigation (HVM) is certainly high on the list. Given the changing threat landscape, vendors have, out of necessity, been driven to adopt more robust and innovative approaches here. In the UK, for example, the Glasgow Airport attack of 2007 was one of the events that acted as a catalyst for new thinking.
Over in the Middle East, Ali Al-Sohaini, the Regional Manager with Frontier Pitts, also reports a change of gear over time for HVM solutions, he says: “Everything is getting cleverer because terrorists are becoming accustomed to the equipment, and technology, and the nature of vehicle-borne attacks is changing.” To illustrate his point, Al-Sohaini continues that whereas, previously, installing one standard gate might have been enough of a deterrent now on large sites in the region there is more likely to be a gate, and behind it some bollards or a blocker, interlocked to another gate, linked to alarms, access control, and even the local police station.
Added to this, Al-Sohaini says that kerb appeal – or aesthetics – is becoming a key part of the hostile vehicle mitigation equation, especially for prestige projects: “As you can imagine when you have a multi-million pound tower, with beautiful finishes, the last thing that anyone wants is a mass of metal at the front.” Al-Sohaini points to one approach that Frontier Pitts has taken with static and hydraulic bollards: “The application of a stainless steel sleeve with a mirror finish is helping them [the bollards] blend into their environment.” From a practical perspective, shallow mount-based HVM solutions are also finding favour for cities and airports where, says Al-Sohaini, digging deep – or extensive works – is simply not an option.
Rise of the robots
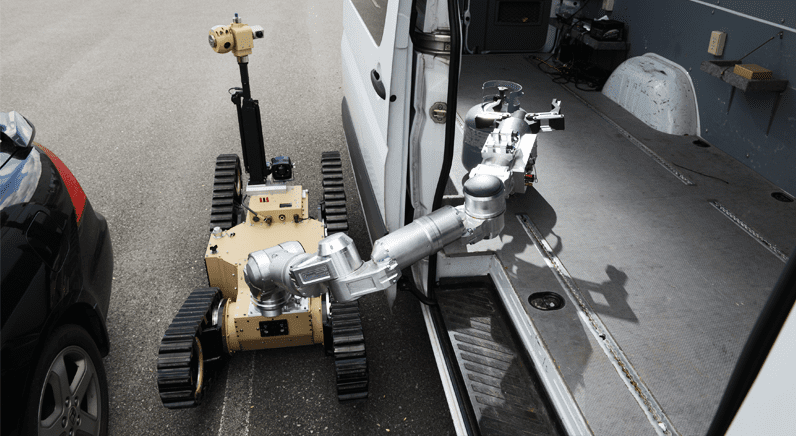
Another solution that has had to mirror the trajectory of the terrorist threat over several decades – and, hints at what the future holds technology-wise – is the EOD [Explosive Ordinance Disposal] robot. Without doubt the latest EOD robot models are much more capable than those first deployed in environments like Northern Ireland during ‘the Troubles’ which, in reality, had more in common with agricultural machinery. Now we are seeing state-of-the art EOD robots being rolled out for use by bomb disposal teams featuring: specialised robotic arms that provide multiple degrees of freedom; integrated payload bays, and the ability to deal with suspicious items in more confined locations.
Mark Kauchak, the Director of Sales and Customer Support at Northrop Grumman Remotec, tells me more about the added dimension that the latest robotic arms, for example, offer to operators who can control them remotely: “With [an arm’s] additional degrees of freedom you are working more in three dimensions.” Touching on other factors influencing EOD robot development, Kauchak continues: “We have seen increases in computing power and improvements in motors and communications. Ten years ago what was available drove robots towards a certain type of design but, with various advances, they enable you to do more and different things for end users.”
Dealing with drones
One security aspect, definitely gaining more traction month-by-month, comes in the form of systems to detect – and deter – the soaring number of drones in our skies which accidentally, or deliberately, are venturing close to areas where they simply should not be. Examples of drone activity that has given the authorities and site operators cause for concern range from the multiple reports of unidentified drones flying near French nuclear power stations to near misses with civilian aircraft coming into land.
In terms of a practical answer to the drone or UAV (Unmanned Aerial Vehicle) dilemma, one take on this centres around the aptly named DroneTracker from Dedrone. Basically this is a multi-sensor drone warning system which, Dedrone reckons, reflects the reality that the size, speed, and shape of drones make identification extremely difficult for a single monitoring method. Utilising a system of interacting sensors the DroneTracker is designed to reliably detect all types of drones based on multiple parameters such as noise, shape, and movement patterns, with the processing done in the device itself or via cloud computing. The DroneTracker’s built-in HD (High Definition) camera allows the saving of images and video so there is evidence of the intrusion.
Sky high
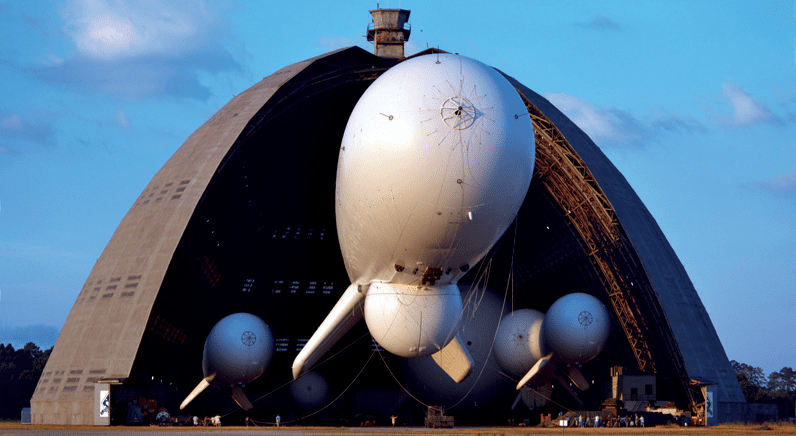
Although perhaps not hitting the headlines in the same way as drones, either positively or negatively, aerostats – commonly known as blimps – are coming to the fore more and more from a border monitoring perspective and to protect critical infrastructure and sporting venues as was the case in Rio.
The takeaway message is that aerostats can no longer be thought of as just the preserve of the military or old technology that has had its day. Those who develop the solutions, and users like the US CBP (Customs and Border Protection), stress that aerostats can offer a sophisticated form of persistent surveillance that other aerial platforms simply struggle to deliver.
Speaking to Matthew McNeil, VP Business Development, at US-based TCOM about the dynamics of aerostat development and the sensors they carry, McNeil replies: “As technologies that combine big data, analytics, and infrared and telecommunications, advance, lighter-than-air tactical aerostat platforms can be leveraged for ISR [Intelligence, Surveillance and Reconnaissance] applications.” McNeil adds that technologies designed for the battlefield are also perfectly suited to address threats to ‘the homeland’ and can be readily applied to solve, and alleviate, the duties of domestic first responders.
Active CCTV algorithms
Turning to another aspect of security, the situation for video analytics is very much on the up as it starts to win adherents after a series of false dawns were, sadly, solutions were over-hyped and, when deployed, struggled to live up to their star billing. As times have changed, video analytics – or Video Content Analysis (VCA) – is being approached in a more accurate and down-to-earth manner.
One vendor has refined video analytics for retail outlets to the point where it can flag up specific behaviour around scan avoidance, at manned and self-checkout areas, with a high degree of accuracy. Interestingly, Malay Kundu, from StopLift Checkout Vision Systems – the leading player in this field – cut his teeth in facial recognition systems in airports and says that StopLift itself actually grew out of a Harvard Business School research study ‘Project StopLift’ on ‘Retail Loss Prevention’. This was an effort which he reckons has stood him in good stead for the challenges found in today’s retail environment: “We are applying a lot of really hard-core high tech here. That is how we are able to detect ‘sweet-hearting’ [where there is collusion between employees and customers] and generally scan avoidance. We are doing a ton of this kind of stuff for manned checkouts as well as self-checkouts.”
Controlling access
In terms of how access control has developed, Philippe Huysman, Global Portfolio Manager Access Control, Siemens Building Technologies, says that he has been involved with physical access control systems for the past 15 years: “During this timeframe access control systems have evolved from being standalone access control systems running on separate proprietary, mainly serial, communications to integrated security management systems incorporating video, intrusion, perimeter protection and analytics, running on IT networks and infrastructures,” explains Huysman.
Huysman believes that the emergence of smart cards has opened up new opportunities: “It has enabled the use of the card beyond access control. Cards that had previously carried data to allow access to the building are now being used for multiple applications. These can range from parking to electronic cashless purchase of food, with the potential to enhance workplace security through the inclusion of authentication for accessing the IT network and applications, digital signature and email encryption, biometric data and printer access management.”
He goes on to say that the introduction of offline and wireless electronic door fittings has also contributed significantly to the growth of access control in recent years: “This has allowed us to extend electronic access control to encompass low traffic or lower-level security access points, which in the past were not economically viable for online systems,” concludes Huysman.
Intelligent integration
In this ‘Internet of Things’ world, David Aindow, Product and Technology Director at Synectics, feels that moving ahead, greater attention is going to be paid to solutions – from CCTV to access control – that can operate in an integrated way rather than, simply, being confined to disparate and unconnected silos: “There is a big emphasis on integration and bringing not just alerts of events but situational data into a command and control platform.”
Aindow emphasises that, ultimately, it is about how people assess the levels of threats that might be coming from different sources and then driving operators through procedures, and work flows, to make sure that they are handling all of the events in the most efficient way possible.
From physical to cybersecurity
Of course any focus on the evolution of security would not be complete without referencing cybersecurity in some shape or form. With the move to IP-based video surveillance and access control solutions the cyber and physical security system worlds have never seemed closer so it is perhaps not too surprising that, over recent months, we have seen a string of announcements from vendors regarding the steps they are taking in this area.
One development of note here was the unveiling by Tyco Security Products – back in April – of an ambitious Cyber Protection Programme. This multi-faceted initiative, according to Tyco, is designed to take a holistic approach to cybersecurity protection for physical security with each phase of the product development life cycle very much in the programme’s sights.
Virtual threats

Hodson concludes by expanding on this theme by warning that, given such developments, traditional defence mechanisms are insufficient or ineffective against today’s methods of cybercrime: “If you take advanced malware, relying on signature-based detection, like we did five years ago, ten years ago – won’t do. The traditional blacklist approach only kind of worked when the bad guys were releasing malware every week every month however we are now seeing them release new hashes of malware every minute. The average life of a malware hash is something like 58 seconds.”
[su_button url=”https://www.securitynewsdesk.com/newspaper/” target=”blank” style=”flat” background=”#df2027″ color=”#ffffff” size=”10″ radius=”0″ icon=”icon: arrow-circle-right”]For more stories like this click here for the Security News Desk Newspaper[/su_button]